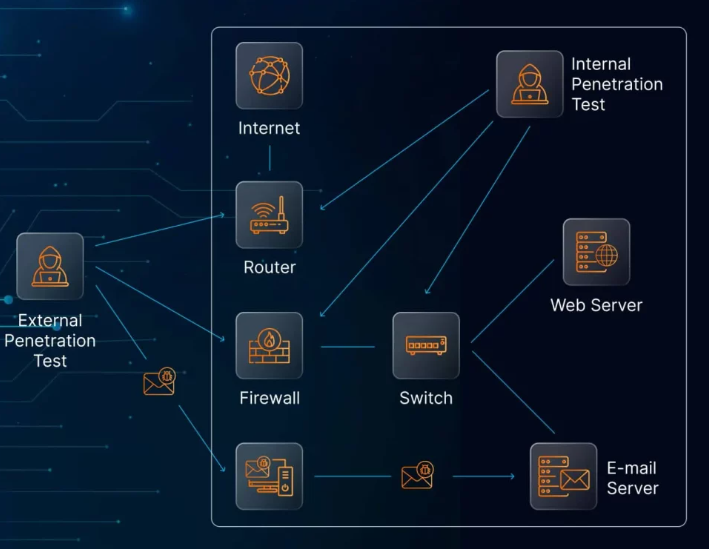
Penetration testing, often referred to as ethical hacking, is a crucial method used to evaluate an organization’s security defenses. This process involves simulating the techniques of real-world cybercriminals to identify vulnerabilities that could be exploited. It covers a wide range of attack scenarios, including external threats (black-box testing), internal threats (grey-box testing), and attacks from within the organization (white-box testing). Unlike vulnerability assessments, which focus on automated tools, penetration tests involve manual testing to discover deeper flaws, with the goal of revealing as many vulnerabilities as possible.
Penetration tests are essential for organizations, not only to identify weaknesses but also to assess their ability to withstand potential cyberattacks. These tests help prevent serious business disruptions, such as the theft of sensitive data or the compromise of critical systems. Moreover, they are key to maintaining compliance with cybersecurity laws and industry regulations.
The Phases of Penetration Testing
Penetration testing follows a structured process, divided into multiple phases that mirror real-world attack strategies. While the exact phases may vary slightly depending on the methodology, the following are the core stages involved in most penetration testing engagements.
1. Pre-Engagement Planning
The first phase sets the foundation for the entire penetration test. During this stage, critical parameters are established, such as the scope of the test, which assets are included, and which are excluded. The level of access (black-box, grey-box, or white-box) is determined, along with the start and end dates for the engagement. It’s also during this phase that communication channels are set up for reporting vulnerabilities with critical severity. A clear understanding between the penetration testers and the organization helps ensure expectations are aligned, and access is granted for the testing phase.
2. Reconnaissance
Reconnaissance is the phase where penetration testers begin gathering as much information as possible about the target’s systems. This stage involves both passive and active techniques.
- Passive Reconnaissance involves collecting publicly available information through open-source intelligence (OSINT) without directly interacting with the target system. This could include details such as domain names and IP addresses.
- Active Reconnaissance involves making direct network requests to probe the system, revealing details about the technology stack and software versions. This information is valuable for identifying entry points and vulnerabilities.
3. Scanning
In this phase, penetration testers perform automated scans to identify live assets and open ports on the network. The purpose is to broaden the potential attack surface by finding additional entry points. For example, if a new service is discovered through port scanning, testers will attempt to identify weaknesses within that service. This phase may also involve a vulnerability assessment to quickly pinpoint flaws, misconfigurations, or outdated software, all of which could serve as potential gateways for a hacker.
4. Gaining Access
This phase marks the first attempt to exploit the vulnerabilities identified during previous steps. The penetration tester attempts to breach the system using the discovered weaknesses, evaluating how effective security measures are in preventing unauthorized access. If successful, the tester continues to test other entry points and attempts to escalate their privileges. The focus at this stage is on gaining access to critical systems and assessing the impact of a successful attack.
5. Maintaining Access
Once access is gained, the tester attempts to establish persistent access within the system. While this may not always be a requirement, in some cases, testers simulate advanced persistent threats (APT) by ensuring continued access. Techniques may involve hiding malicious code in system processes or compromising network devices. The purpose is to understand how an attacker might remain undetected for long periods. During this phase, testers may also perform lateral movement across the network to find and exploit additional vulnerabilities.
6. Covering Tracks
After successfully gaining and maintaining access, the next task is to cover any traces left behind during the attack. This phase involves removing test software, clearing logs, and undoing any changes made to the system to restore it to its original state. The goal is to ensure that no evidence remains that could lead to the identification of the penetration testers or the methods used in the engagement. This phase is crucial for preventing the inadvertent triggering of malicious payloads or leaving exploitable remnants in the system.
7. Reporting
The final phase involves documenting all findings from the penetration test. A detailed report is provided, which includes an executive summary, technical findings, and recommendations for remediation. This report highlights the vulnerabilities found, their severity, and the impact of potential exploitation. It also outlines suggested corrective actions and strategies for preventing future attacks. The findings help the organization strengthen its security posture and meet compliance requirements.
Why Penetration Testing Matters
Penetration testing is more than just identifying flaws; it’s a critical tool for improving an organization’s overall cybersecurity strategy. Regular testing allows organizations to uncover weaknesses before cybercriminals can exploit them, preventing costly data breaches and system compromises. The insights gained from penetration testing can inform security policy, guide vulnerability management, and help safeguard sensitive data. Additionally, testing helps organizations stay compliant with cybersecurity standards and regulations, which is crucial for maintaining trust with customers and partners.
By simulating real-world attacks, penetration testing offers an opportunity to see how well your security infrastructure holds up against sophisticated threat actors. It provides valuable knowledge to security teams, helping them stay ahead of evolving cyber threats and continuously improving their defenses.
Strengthen Your Cybersecurity with Penetration Testing
Penetration testing is an essential tool in modern cybersecurity strategies. By mimicking the methods used by hackers, organizations can gain a better understanding of their vulnerabilities and take proactive steps to protect their critical assets. Ready to boost your cybersecurity? Consider booking a session with a trusted penetration testing expert today.