As cyber threats continue to evolve, the European Union’s NIS2 Directive is pushing organizations to adopt more stringent security practices. For businesses operating in sectors critical to society and the economy, this means rethinking how they approach cybersecurity. One key aspect of this approach is penetration testing—an essential measure to ensure both regulatory compliance and long-term resilience against cyber attacks.
Understanding NIS2 and Its Security Implications
NIS2 sets forth enhanced cybersecurity expectations for essential and important entities. These include sectors such as finance, healthcare, digital infrastructure, and transport. The directive mandates that organizations establish strong risk management frameworks and adopt technical, operational, and organizational controls to secure their digital ecosystems.
Among these controls is the requirement to conduct regular security assessments—including penetration testing—to proactively identify and address vulnerabilities in network and information systems.
The Role of Penetration Testing in NIS2 Compliance
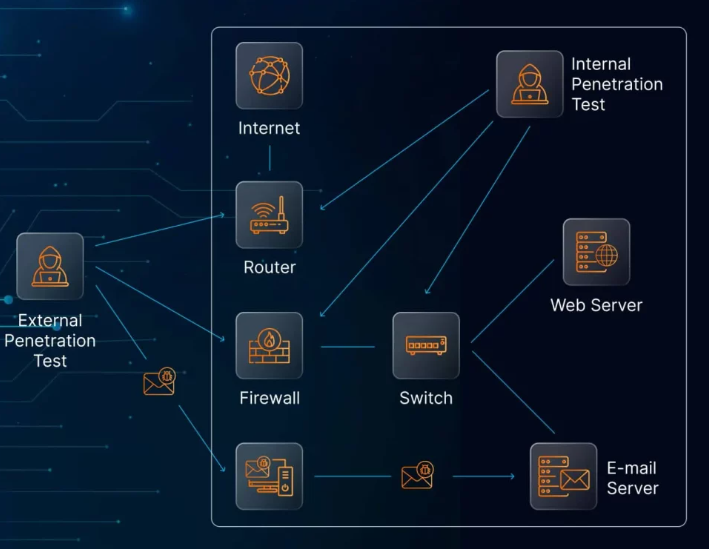
Penetration testing, often referred to as ethical hacking, involves simulating real-world cyber attacks to discover weak points in an organization’s digital defenses. Unlike automated scans that merely flag known vulnerabilities, penetration tests provide a more realistic view of how an attacker could infiltrate a system and what damage they could potentially cause.
By incorporating this practice into their cybersecurity programs, organizations can:
- Detect hidden vulnerabilities before they’re exploited
- Meet regulatory requirements under NIS2
- Improve incident response readiness
- Show commitment to cybersecurity diligence
Who Needs to Comply with NIS2?
The directive applies to a broad range of organizations deemed essential or important to national infrastructure. This includes digital service providers, healthcare institutions, financial companies, energy suppliers, and even emerging sectors such as space technology and cloud platforms.
Businesses that fall under these categories must implement a penetration testing strategy that aligns with NIS2’s core security objectives. This isn’t just about meeting legal obligations—it’s about building a resilient infrastructure capable of withstanding modern threats.
Why Pen Testing Is More Than Just a Requirement
While regulatory adherence is important, penetration testing brings significant value beyond compliance. It allows businesses to stay a step ahead of attackers by continuously validating their defenses. This leads to better risk prioritization, faster detection and response, and reduced likelihood of operational disruptions.
Moreover, the financial repercussions of a breach—both in terms of monetary loss and reputational damage—far outweigh the cost of routine security testing. A well-executed penetration testing program serves as both a preventive measure and a strategic investment.
How Frequently Should Testing Be Done?
There’s no universal answer, but best practices suggest:
- At least once a year
- After major system updates or infrastructure changes
- More frequently for high-risk sectors or if the threat landscape intensifies
The goal is to ensure that security controls are not only in place but are also functioning as intended under realistic attack scenarios.
Building a Stronger Cybersecurity Posture
Penetration testing helps organizations develop a more adaptive and robust cybersecurity framework. Here’s how:
- Realistic threat simulations: Test how systems respond to actual attacker behaviors
- Improved detection and response: Uncover gaps in security operations
- Prevention of breaches: Identify risks early, avoid financial losses
- Continuous improvement: Adapt to new threats through periodic testing
Treating pen testing as a one-time task is a common mistake. Cybersecurity must be approached as an ongoing process that evolves alongside technological and threat advancements.
Common Challenges and How to Overcome Them
Many companies struggle with penetration testing due to limited expertise or budget constraints. Partnering with a reputable Managed Security Services Provider (MSSP) can bridge this gap. These providers offer specialized testing, clear reporting, and actionable recommendations that are crucial for both fixing issues and maintaining NIS2 compliance.
Another challenge is post-test follow-through. Too often, businesses don’t fully act on findings from a penetration test. Prioritizing vulnerabilities, implementing fixes, and verifying results through retesting are critical steps that should not be overlooked.
Best Practices for Effective Testing
To make the most out of penetration testing efforts, organizations should:
- Test proactively – Go beyond compliance and test regularly
- Set clear objectives – Define what systems and processes will be tested
- Use a hybrid approach – Combine automated scans with manual analysis for deeper insights
- Act on results – Don’t just collect reports; use them to improve defenses
- Engage certified professionals – Work with experts who understand NIS2 and hold recognized credentials like OSCP or CISSP
Final Takeaway
The NIS2 Directive is reshaping how organizations think about cybersecurity. Penetration testing plays a pivotal role in this shift—not just as a compliance measure but as a critical component of a broader resilience strategy.
By embracing regular, expert-led pen testing, companies can build stronger defenses, reduce cyber risks, and stay ahead in an increasingly hostile digital environment. The path to compliance is also a path to greater security—and now is the time to walk it.