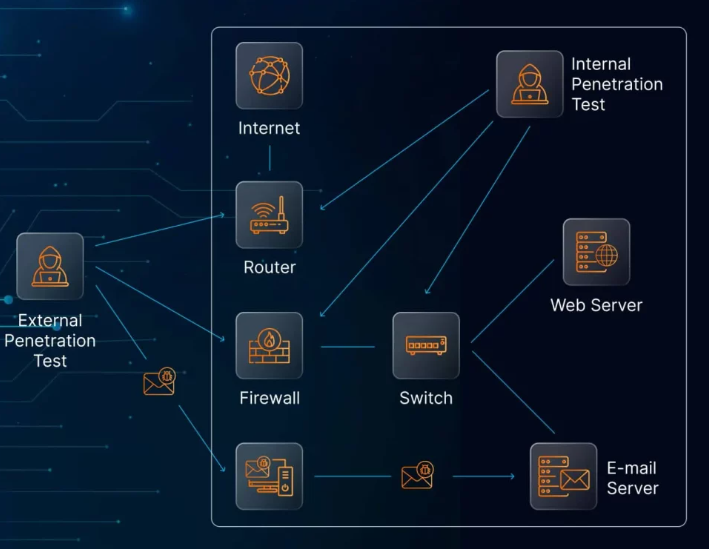
After completing a penetration test and addressing the identified vulnerabilities, how can you be certain that the fixes are effective? This is where the process of retesting becomes crucial. Retesting ensures that the changes made have truly resolved the issues, verify that no new vulnerabilities have been introduced, and uncover any deeper issues that may have been overlooked. In this blog, we’ll break down the importance of retesting, the steps involved, and how to effectively validate your fixes to strengthen your security posture.
What is Retesting?
Retesting, or remediation validation testing, is an essential follow-up process that confirms whether the vulnerabilities identified in a penetration test have been adequately fixed. The goal isn’t just to confirm that fixes have been applied but to ensure that these actions haven’t inadvertently caused new problems. Retesting focuses on re-evaluating the original vulnerabilities, often using the same testing methods and tools to ensure consistency and accuracy in the results.
Why Retesting Matters
Retesting plays a critical role in maintaining and strengthening your security defenses. Here’s why it’s necessary:
- Confirm remediation success: Ensures that all vulnerabilities from the initial test have been fully addressed.
- Detect incomplete fixes: Identifies misconfigurations or partial fixes that could leave the system exposed.
- Check for new vulnerabilities: Tests for any new issues that might have been introduced during the remediation process.
- Uncover systemic issues: Finds underlying causes that could potentially lead to the recurrence of similar vulnerabilities.
How to Prepare for Retesting
Preparation is key to a successful retesting process. Proper planning ensures the right information is gathered, the scope is clearly defined, and the environment is ready for testing. Here’s a checklist to help:
- Gather information:
- Review the initial penetration test report, identifying vulnerabilities and their severity.
- Collect documentation on the remediation actions taken, such as patch notes, configuration changes, and update logs.
- Confirm that remediation efforts were completed on schedule and according to expectations.
- Plan the retesting phase:
- Define the scope, whether you’re retesting all vulnerabilities or focusing on critical issues.
- Coordinate with technical teams to align retesting with completed remediation efforts.
- Prepare the testing environment to mirror conditions from the original test and ensure systems are stable and accessible for testing.
- Essential Documents and Tools:
- Review the penetration test report and remediation logs.
- Ensure you have the security testing tools used in the original test.
- Set up test accounts, permissions, and backup processes to minimize risk during retesting.
Conducting the Retesting Process
Once preparation is complete, the retesting phase can begin. This phase ensures that the fixes were effective and that no new vulnerabilities were introduced. Follow these steps to carry out retesting:
- Reassess Identified Vulnerabilities
- Focus on previously identified vulnerabilities using the same tools and techniques from the original test.
- Verify that each vulnerability has been fully addressed and resolved.
- Test for Regression Issues
- Test for new vulnerabilities caused by the remediation efforts.
- Examine systems, configurations, or processes that might have been affected by the fixes, ensuring that the changes didn’t introduce new risks.
- Investigate Related Areas
- Extend the testing to other assets or systems that could share similar vulnerabilities.
- Conduct tests in areas impacted by the fixes to ensure comprehensive coverage.
- Collaborate with Technical Teams
- Work closely with the teams who applied the fixes to address any lingering issues or newly discovered vulnerabilities.
- Refine the remediation process together if necessary.
- Document and Report Findings
- Create a detailed report comparing the retesting results to the initial vulnerabilities.
- Include evidence such as screenshots, logs, and tool outputs to validate the fixes.
Best Practices for Retesting
To make your retesting process as effective as possible, keep these best practices in mind:
- Maintain consistency: Use the same tools and techniques from the original test for accurate comparisons.
- Prioritize high-risk vulnerabilities: Focus on addressing the issues that pose the greatest risk to your organization’s security.
- Verify the fixes: Ensure the fixes were applied correctly at the appropriate levels (e.g., application-level or server-level).
- Document every step: Keep detailed records of each step, including methods, findings, and evidence for future audits.
- Ensure clear communication: Foster open collaboration between security experts and technical teams to resolve issues during retesting.
Analyzing and Interpreting Retesting Results
Once retesting is complete, it’s time to analyze the results and interpret them effectively. Here’s how:
- Compare with the original report: Ensure that the identified vulnerabilities have been resolved.
- Identify unresolved issues or new vulnerabilities: Look for any remaining issues or new vulnerabilities introduced during remediation.
- Assess improvements: Evaluate how well the fixes have strengthened your overall security posture.
Post-Retesting Activities
Retesting isn’t the final step. Use the results to further enhance your cybersecurity strategy:
- Update security policies: Revise your security protocols to incorporate lessons learned from the retesting phase.
- Implement additional controls: Introduce new security measures, such as stronger authentication or monitoring tools, as necessary.
- Ongoing monitoring: Establish a continuous monitoring plan to detect new threats in real-time and track the effectiveness of your fixes.
Why Choose AMATAS for Penetration Testing and Retesting?
At AMATAS, we understand the importance of retesting to ensure the effectiveness of your security fixes. That’s why we include two retests after every penetration test at no additional cost, ensuring that your remediation efforts are validated and no gaps remain in your defenses.
Common Challenges in Retesting
While retesting is essential, it comes with its own set of challenges:
- Incomplete remediation: Some fixes may not fully address the root cause, leaving the system exposed.
- Lack of resources: Limited access to skilled professionals or necessary tools may hinder thorough retesting.
- Prioritization: Determining which vulnerabilities to prioritize can be difficult, but using frameworks like Continuous Threat Exposure Management (CTEM) can help.
Conclusion
Retesting is more than just a follow-up to penetration testing – it’s an essential process that ensures your security fixes are effective and your organization remains resilient against evolving threats. By following the steps outlined here, you can validate your remediation efforts, uncover any remaining risks, and strengthen your defenses against future cyber threats. Remember, cybersecurity is an ongoing journey, and regular penetration testing, retesting, and monitoring are key to maintaining a secure organization.