Healthcare organizations are tasked with safeguarding sensitive health data, and the HIPAA Security Rule provides the framework for doing so. However, complying with its requirements can be overwhelming for many, particularly with the increasing complexity of cyber threats and regulatory expectations. In this blog, we’ll break down what the HIPAA Security Rule requires and how partnering with a managed cybersecurity service can streamline the process, making it more manageable while enhancing your overall security.
What is the HIPAA Security Rule?
The HIPAA Security Rule is a critical aspect of the Health Insurance Portability and Accountability Act (HIPAA), designed to protect electronic protected health information (ePHI). While the HIPAA Privacy Rule focuses on the use and sharing of protected health information (PHI), the Security Rule sets standards for how to secure ePHI through administrative, physical, and technical safeguards.
The Security Rule applies to all covered entities (like healthcare providers, health insurers, and healthcare clearinghouses) and their business associates (such as IT vendors and cloud service providers who manage ePHI). The goal is to:
- Maintain the confidentiality of patient data.
- Ensure the integrity of the data, preventing unauthorized changes.
- Make sure authorized users can access the data when needed.
To meet these goals, the Security Rule outlines three main categories of safeguards:
- Administrative Safeguards: These include policies and procedures to manage security measures and employee conduct.
- Physical Safeguards: Measures to protect systems and facilities from unauthorized physical access.
- Technical Safeguards: The use of technology to secure ePHI, including encryption, access control, and monitoring.
In essence, the Security Rule requires a comprehensive and risk-based approach to protecting healthcare data, demanding both expertise and continuous oversight.
Why Is HIPAA Compliance Challenging?
Though the HIPAA Security Rule’s requirements are clear, many organizations face difficulties implementing them. This is particularly true for small to mid-sized healthcare providers and tech vendors that handle ePHI. Compliance can feel like a moving target—complex, resource-intensive, and risky if not properly managed.
Here are some of the reasons why HIPAA compliance can be so overwhelming:
- Complex Requirements: The Security Rule includes several layers of administrative, physical, and technical safeguards, each with specific standards that require careful interpretation and documentation.
- Lack of In-House Expertise: Many organizations lack the dedicated cybersecurity staff needed to handle compliance tasks. Without a Chief Information Security Officer (CISO) or specialized team, these responsibilities can be poorly managed or deprioritized.
- Evolving Threats: Cyber threats, including ransomware, phishing, and insider threats, are constantly evolving. HIPAA requires that organizations account for these “reasonably anticipated” risks, making compliance a continuous effort rather than a one-time task.
- Risk of Penalties: Non-compliance can lead to hefty fines and damage to an organization’s reputation. This creates immense pressure to get things right.
- Uncertainty About What’s Enough: HIPAA allows flexibility in how safeguards are implemented, which can cause confusion. Questions like, “Is our encryption strong enough?” or “Is our incident response plan adequate?” can leave organizations uncertain about whether they meet the requirements.
This is where managed cybersecurity services like AMATAS can make a significant difference. These services are tailored to meet HIPAA’s safeguard requirements, simplifying compliance and helping organizations manage security risks more effectively.
Breaking Down HIPAA Safeguards and How AMATAS Supports Compliance
Now that we’ve explored the core of the HIPAA Security Rule and the challenges organizations face in achieving compliance, let’s dive deeper into the key safeguard areas. Here’s how AMATAS can support each of these critical components:
- Risk Analysis: HIPAA mandates a comprehensive risk analysis to assess potential vulnerabilities to ePHI. AMATAS provides structured risk assessments, helping prioritize risks and develop mitigation strategies.
- Incident Response Planning: Organizations must have documented procedures for responding to security incidents. AMATAS offers a Virtual CISO service that helps build and implement an incident response plan, while MXDR provides real-time threat detection and response.
- Employee Security Training: Ongoing security training is essential to avoid human errors. AMATAS offers Managed Security Awareness training, equipping staff to recognize phishing attempts and report suspicious activities.
- Access Control and Encryption: HIPAA requires restricting access to ePHI and ensuring it is encrypted both in transit and at rest. AMATAS provides managed IT services to enforce access control policies and ensures that encryption is consistently applied across all systems.
- System Auditing and Monitoring: Regular system audits are necessary to detect suspicious activity. AMATAS’s MXDR service continuously monitors your systems, providing detailed logs and visibility into access patterns to support compliance and forensic investigations.
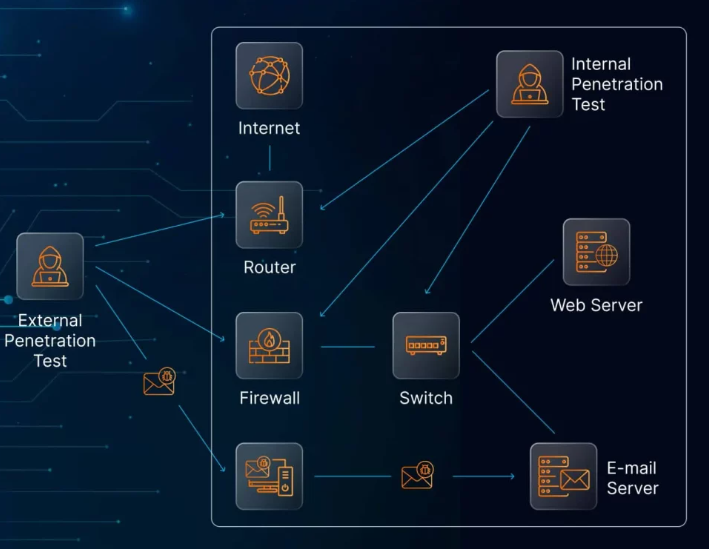
- Penetration Testing and Vulnerability Discovery: Regular testing of security defenses is critical. AMATAS conducts penetration testing to simulate real-world attacks and helps identify weaknesses before they can be exploited.
How Managed Services Simplify HIPAA Compliance
Meeting HIPAA’s requirements internally can be overwhelming, especially for smaller organizations. From creating security policies to managing devices, responding to threats, and training staff, compliance requires constant attention and coordination across multiple areas.
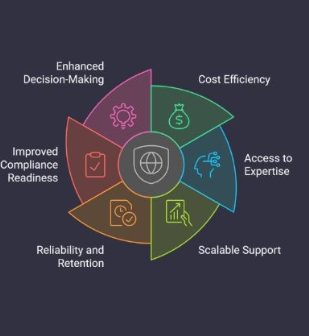
This is where outsourcing cybersecurity management to specialized providers can help. By partnering with a service provider like AMATAS, you can:
- Reduce Complexity: Instead of managing multiple vendors and tools, AMATAS offers an integrated suite of services that directly align with HIPAA’s safeguard requirements.
- Access Expertise: With a Virtual CISO and specialized cybersecurity team, you can meet HIPAA’s complex requirements without having to hire an in-house expert.
- Scale Security Efforts: Whether expanding staff or launching new services, AMATAS’s solutions are designed to scale with your organization, keeping pace with growing security needs.
- Stay Prepared for Threats and Audits: AMATAS helps you detect and respond to security threats in real-time, document compliance efforts, and prepare confidently for audits.
- Transform Compliance into a Value-Added Benefit: Achieving HIPAA compliance can become a competitive advantage, showing clients and partners that you take data security seriously.
Conclusion
Achieving HIPAA compliance doesn’t have to be an impossible task. By leveraging managed cybersecurity services from AMATAS, you can streamline the process and ensure your organization’s security posture is robust and compliant with HIPAA’s safeguard requirements. With the right support, HIPAA compliance can become a seamless part of your operations, protecting sensitive health data while strengthening patient trust and security.