Crafting a robust cybersecurity framework requires more than just basic protection—it calls for an in-depth understanding of both your internal systems and your internet-facing infrastructure. One of the most effective ways to assess your security posture is through penetration testing. By simulating attacks, this process uncovers weaknesses before malicious actors can exploit them.
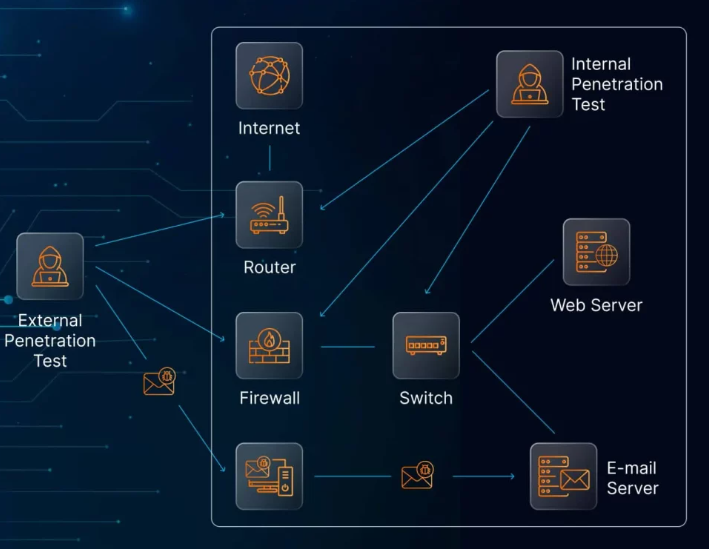
There are two major types of penetration testing: internal and external. Each targets different vulnerabilities and serves a specific purpose. Knowing how they differ and when to use them is key to building a comprehensive defense strategy.
Understanding Penetration Testing
Penetration testing, also known as ethical hacking, involves security professionals mimicking cyberattacks to identify exploitable flaws in your IT environment. Unlike basic vulnerability scans, penetration tests go a step further—they simulate real attacks to determine how deeply those weaknesses could be exploited in the real world.
This form of testing helps organizations improve their security controls by providing clear, actionable feedback. It’s a proactive measure aimed at minimizing risk before any actual damage occurs.
Internal Penetration Testing: Looking Inward
Internal penetration testing evaluates what could happen if a threat actor gained access to your internal network—whether through compromised credentials, rogue insiders, or malware infections. The purpose is to see how far an attacker could go once inside your perimeter.
Key areas assessed in internal testing include:
- Unauthorized privilege escalation
- Movement between systems and network segments
- Access to confidential or sensitive internal data
Common systems evaluated include internal servers, employee endpoints, file shares, and authentication platforms like Active Directory.
This type of testing offers valuable insight into how well your internal safeguards are functioning—things like segmentation, access management, and monitoring controls.
External Penetration Testing: Defending the Perimeter
External penetration testing, on the other hand, targets assets that are exposed to the public internet. These tests simulate how an external attacker might try to breach your defenses without prior access to your internal systems.
Areas typically assessed include:
- Company websites and online applications
- Remote access systems like VPNs or RDP
- Email and DNS servers
- Cloud-based platforms
External testing involves reconnaissance, vulnerability discovery, and selective exploitation to highlight gaps that could enable unauthorized entry. It’s your first line of defense against internet-based attacks.
Comparing the Two: Key Distinctions
While both testing methods aim to uncover vulnerabilities, they approach the problem from different perspectives:
- Origin of Attack: Internal tests simulate threats from within; external tests simulate attacks from outside.
- Main Focus: Internal testing explores post-breach scenarios; external testing prevents initial breaches.
- Test Targets: Internal focuses on workstations, internal apps, and internal infrastructure; external focuses on websites, servers, and cloud assets.
- Risk Types: Internal reveals risks like privilege escalation and insider threats; external reveals exposed services and misconfigurations.
When to Conduct Internal Penetration Tests
Internal testing is especially useful when:
- You want to examine risks posed by current or former employees.
- Your organization has undergone IT changes or restructuring.
- You’re validating internal access controls and data segregation.
- Regulatory frameworks require it.
Industries with complex infrastructures—such as healthcare, finance, and tech—often conduct regular internal assessments to stay secure and compliant.
When External Testing Is Essential
External testing is appropriate when:
- Launching new digital products or services.
- Maintaining secure public-facing platforms is a business necessity.
- You must meet compliance mandates that require perimeter assessments.
- Your organization wants to prove its cybersecurity commitment to clients.
This form of testing provides early detection of internet-based vulnerabilities that could lead to major breaches.
Why a Combined Approach Is Best
To fully protect your organization, relying on only one type of test isn’t enough. A well-rounded security strategy incorporates both. External testing blocks outside threats, while internal testing ensures any breaches are contained quickly.
By combining both, you can:
- Detect flaws on both sides of the network perimeter.
- Meet broader regulatory and industry requirements.
- Strengthen your response plan across the entire attack surface.
A Partner That Covers All Angles
For many organizations, managing both internal and external testing can be complex. That’s where working with an experienced cybersecurity provider becomes crucial. A knowledgeable partner can tailor testing approaches to your infrastructure, risk level, and regulatory requirements.
With a team that understands both attack simulation and business impact, you get assessments that go beyond technical findings—you get clear, actionable steps toward stronger security.
Final Thoughts
Internal and external penetration tests serve different but equally important roles. While external testing secures your digital front door, internal testing ensures attackers can’t freely move around if they get inside.
Together, they provide a comprehensive view of your organization’s defenses—helping you close security gaps, meet compliance goals, and stay resilient in the face of evolving threats. Choosing to prioritize both isn’t just smart security—it’s smart business.