In today’s digital economy, cybersecurity is no longer a background operation—it’s central to business sustainability. As companies invest in innovation and digital transformation, aligning cybersecurity with broader strategic goals becomes essential. Unfortunately, many organizations still struggle to integrate security initiatives with their core business planning, resulting in fragmented efforts that leave them vulnerable to threats.
While most leaders acknowledge the importance of cybersecurity, there’s often a disconnect between intention and execution. This gap can hinder innovation, delay projects, and erode stakeholder trust. In this article, we explore how organizations can bridge that divide, adopt a strategic view of cybersecurity, and embed it into their long-term growth plans.
Cybersecurity: More Than a Technical Concern
The traditional perception of cybersecurity as a purely technical issue is outdated. It now directly affects business outcomes—impacting customer trust, revenue continuity, and competitive edge. When cyber strategy is aligned with business objectives, it empowers organizations to pursue innovation with reduced risk.
Organizations that view cybersecurity as a business driver can:
- Make risk-informed decisions about new investments and digital products
- Reduce the impact and recovery time of potential breaches
- Promote a strong security culture across all levels of the organization
- Strengthen relationships with customers and regulators through transparency and trust
Where Security and Strategy Often Fall Out of Sync
The disconnect typically stems from a lack of shared understanding between IT security teams and executive leadership. While business leaders focus on outcomes like growth and profitability, security teams often operate within a framework of technical controls and compliance. This misalignment can lead to missed priorities, inefficient spending, and inadequate risk management.
Common issues include:
- Security planning that doesn’t reflect business goals
- Confusing or overly technical communication of risk
- Metrics that don’t support executive decision-making
- Compliance-driven efforts that don’t cover real-world threats
Principles for Bridging the Divide
To close the gap between cybersecurity and business strategy, organizations should focus on the following core principles:
1. Prioritize Based on Risk Impact
Frame security planning around risks that could disrupt business operations. Whether it’s protecting customer data, ensuring system uptime, or avoiding regulatory penalties, identify areas where a breach would have the most serious consequences.
2. Make Risk Assessment an Ongoing Process
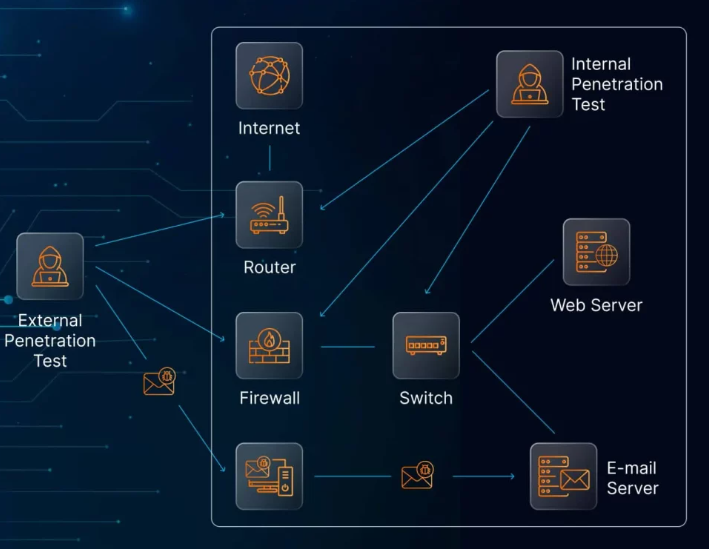
Static, annual audits won’t keep pace with a dynamic threat landscape. Regular assessments—supported by penetration testing and real-time monitoring—enable businesses to proactively identify new risks and adapt their strategies accordingly.
3. Engage Decision-Makers Early
Cybersecurity should be part of strategic conversations from the outset. Whether planning a merger, launching a product, or expanding into new markets, involving executive leaders ensures that security is factored into every decision.
4. Set Metrics Everyone Understands
Effective alignment requires performance indicators that make sense to both business and technical teams. Use metrics like incident response time, risk reduction percentage, and system vulnerability rates to track and communicate progress.
5. Focus on Value, Not Just Cost
Security spending should reflect business value. Invest in initiatives that support customer satisfaction, secure digital offerings, and protect critical infrastructure. This helps shift perceptions of cybersecurity from a cost burden to a strategic advantage.
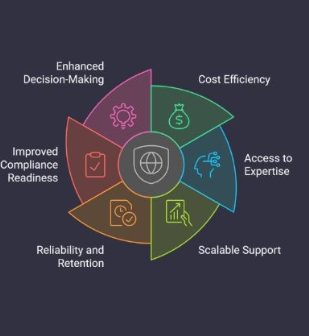
For organizations with limited internal resources, working with outside experts can fill gaps and accelerate progress. A virtual Chief Information Security Officer (vCISO) can offer the expertise needed to guide planning, oversee compliance, and align security programs with long-term business goals—without the expense of a full-time executive.
Tactical Steps to Strengthen Alignment
To operationalize cybersecurity as a strategic enabler, businesses should adopt practices that embed security thinking into every aspect of their operations. These include:
1. Include Security in Strategic Business Planning
Cybersecurity shouldn’t be an afterthought. Evaluate threats and vulnerabilities as part of your broader planning efforts. Tailor strategies to reflect your company’s data handling, infrastructure, and third-party relationships.
2. Perform Routine Testing and Reviews
Penetration tests, threat modeling, and ongoing risk reviews are essential tools. They uncover weak points before they become major problems and help refine security tactics to match evolving risks.
3. Implement Multi-Layered Defenses
A well-rounded security program includes layered protections—from firewalls and encryption to identity management and endpoint monitoring. This “defense-in-depth” model reduces the chance of a single failure compromising the entire system.
4. Build an Effective Incident Response Plan
Have a documented response protocol in place, complete with clear responsibilities and recovery procedures. In a cyber incident, speed and coordination can make the difference between a quick resolution and a costly crisis.
5. Align Budgets with Business Priorities
Don’t treat cybersecurity as a compliance checkbox. Tie investments to specific business outcomes such as product reliability, data protection, or market reputation. This creates more meaningful conversations around funding and accountability.
6. Improve Executive Communication
Translate technical findings into business language. Instead of detailing system vulnerabilities, explain how they impact customer experience, regulatory standing, or operational resilience.
7. Promote a Culture of Security
Security isn’t just a job for IT—it’s a responsibility shared by everyone. Train staff at all levels, foster collaboration across departments, and encourage secure behavior in day-to-day operations.
When External Expertise Adds Value
For organizations that lack experienced leadership in cybersecurity, engaging a vCISO can provide a strategic advantage. This model delivers executive-level guidance without the commitment of a permanent hire, helping businesses stay compliant, make risk-based decisions, and mature their security programs faster.
Scenarios where vCISO services are especially helpful include:
- Navigating new regulations and frameworks
- Translating technical needs for the board
- Aligning IT controls with growth strategies
- Supporting small or midsize teams with limited bandwidth
Warning Signs of Misalignment
If you’re unsure whether your current approach is effectively integrated, here are some red flags to watch for:
- Security initiatives are developed separately from business planning
- Risk discussions focus on technical jargon, not business relevance
- Most activity is driven by compliance deadlines rather than real-world threats
- It’s unclear how security investments contribute to business success
- There’s no consistent tracking of employee engagement or incident response readiness
Recognizing these patterns is the first step toward building a better-aligned, more resilient organization.
Conclusion: Security as a Strategic Imperative
Success in today’s digital world demands more than just patching vulnerabilities—it requires embedding security into your business DNA. When cybersecurity is treated as a strategic asset, organizations can innovate boldly, respond effectively to threats, and earn lasting trust from customers and partners.
Whether you choose to strengthen internal capabilities or leverage external support, aligning your cybersecurity program with business objectives is a smart investment in long-term resilience and growth.