As cyber threats become increasingly prevalent, businesses across various industries—from banking to transportation—are experiencing disruptions due to digital security breaches. The growing risks associated with Information and Communication Technology (ICT) threaten the stability of the EU’s financial system. To counter this, the European Union has introduced the Digital Operational Resilience Act (DORA), which aims to enhance the security of ICT systems within the financial sector.
This article provides an in-depth look at the Digital Operational Resilience Act (DORA), breaking down its key requirements, its implications for the financial sector, and how organizations can achieve compliance.
What Is DORA and Why Does It Matter?
DORA is a new regulation that came into effect on January 16, 2023, with enforcement starting on January 17, 2025. It is designed to protect the financial stability of the EU by ensuring that financial institutions are resilient against ICT-related disruptions. This law mandates that financial entities must bolster their digital security and take proactive measures to identify and respond to cyber risks effectively.
At its core, DORA focuses on preventing cyber attacks in the financial sector and ensuring that organizations are prepared to defend against, recover from, and respond to ICT disruptions. The regulation provides a set of guidelines that promote improved cybersecurity and resilience for financial services, reinforcing the importance of data protection and system integrity.
Key Requirements of DORA
DORA’s framework is built on five core pillars, each addressing a vital aspect of digital resilience within the financial ecosystem. These are:
1. Risk Management
Financial institutions must develop a comprehensive risk management framework that addresses ICT risks. This involves identifying and mitigating potential cybersecurity threats, ensuring that institutions—whether traditional banks or cryptocurrency service providers—are protected. DORA mandates that firms create disaster recovery plans and implement proper oversight to ensure that critical functions are safeguarded.
2. ICT Incident Reporting
The regulation requires that financial entities report ICT incidents, such as data breaches or system failures, to national authorities. Timely reporting helps authorities track vulnerabilities and bolster the security of the financial sector. Both financial organizations and third-party service providers must adhere to this mandate, as failure to comply could result in penalties.
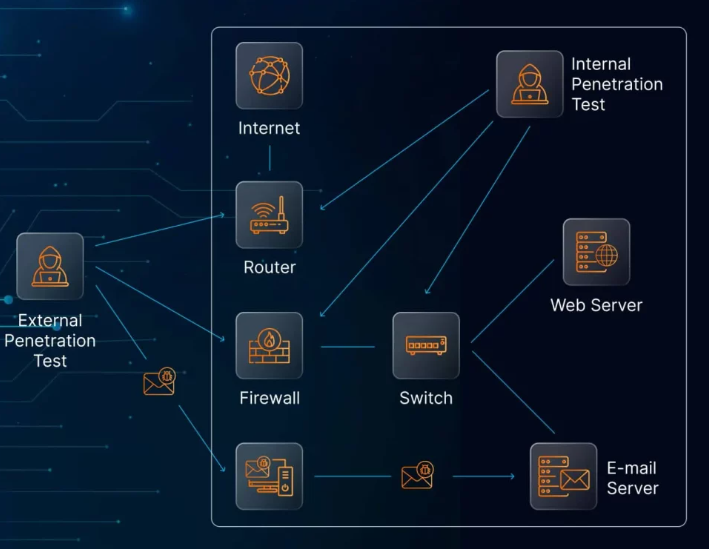
3. Digital Operational Resilience Testing
DORA requires organizations to perform resilience testing, such as penetration tests and risk-based assessments, every three years. These tests evaluate how well an organization can handle ICT-related disruptions and ensure they are prepared for potential cyber incidents. This proactive testing helps institutions meet compliance requirements while strengthening their defenses.
4. Information and Threat Intelligence Sharing
In a collaborative effort to enhance cybersecurity, DORA encourages financial institutions to share threat intelligence with each other. By exchanging insights on emerging threats, organizations can more effectively manage risks and protect themselves from widespread cyber attacks. Sharing this data also helps mitigate the consequences of breaches, ensuring faster compensation for affected customers.
5. ICT Third-Party Risk Management
A crucial component of DORA is managing third-party risks. Financial institutions must assess and monitor the ICT risk management practices of their third-party service providers. DORA requires annual assessments to ensure that these service providers maintain adequate security protocols. Non-compliance can result in penalties for both the financial institutions and their third-party partners.
Who Needs to Comply with DORA?
DORA affects a wide range of entities within the EU financial sector, including banks, insurers, payment processors, investment firms, and more. The regulation also extends to third-party ICT service providers that support these organizations. Even institutions outside the EU that provide services to EU-based firms must comply with DORA.
In addition to traditional financial institutions, other entities like cryptocurrency service providers, electronic money institutions, and reinsurance intermediaries are also subject to DORA’s requirements. Organizations must assess whether they fall under the scope of this regulation and take the necessary steps to comply.
Drawing Parallels with GDPR
The implementation of DORA can be likened to the introduction of the General Data Protection Regulation (GDPR) in 2018. GDPR reshaped how companies handle personal data and protect privacy within the EU. Similarly, DORA aims to enforce stricter security measures for the financial sector, ensuring better protection against ICT-related threats.
Many businesses struggled with GDPR compliance in the early days, facing challenges related to data protection changes. Companies like Google, British Airways, and Marriott International faced significant fines for non-compliance. Likewise, DORA carries the potential for penalties if organizations fail to meet its requirements, with regulators empowered to impose heavy fines.
Steps to Achieve DORA Compliance
Achieving DORA compliance requires a structured approach to managing ICT risks. Below is a checklist to guide organizations in their compliance journey:
1. Determine the Scope of DORA Compliance
Identify whether your organization falls under the scope of DORA. This includes assessing whether your entity is a financial institution, investment firm, or a provider of ICT services to the EU financial sector. Consider which authorities oversee your compliance, such as the European Banking Authority (EBA) or the European Securities and Markets Authority (ESMA).
2. Develop a Digital Operational Resilience Strategy
Create a strategy that covers prevention, detection, response, and recovery from ICT-related incidents. Ensure the strategy aligns with your organization’s broader information security goals and addresses both internal and external threats.
3. Assess and Address ICT Risks
Regularly assess your ICT systems for vulnerabilities and conduct penetration testing and scenario-based assessments. Work with auditors to review the effectiveness of your risk management processes and make necessary adjustments.
4. Secure ICT Assets
Ensure the security of all essential ICT assets, including hardware, software, data, and networks. Implement robust security protocols to protect these assets from breaches and disruptions. Also, ensure that your third-party providers adhere to DORA’s security requirements.
5. Establish an ICT Risk Management Framework
Integrate an ICT risk management framework into your organization’s overall strategy. Define roles and responsibilities for managing risks, and establish oversight processes to ensure compliance with regulatory standards.
6. Create an Incident Response Plan
Develop a formal incident response plan to address disruptions swiftly. The plan should include procedures for identifying, reporting, and resolving ICT incidents, ensuring minimal impact on operations.
7. Continuously Monitor ICT Systems
Use real-time monitoring tools to detect early signs of threats or disruptions. Regular monitoring helps you stay ahead of potential issues and ensures your systems remain secure.
8. Conduct Regular Statutory Audits
Engage with statutory auditors to evaluate the effectiveness of your resilience strategies and identify areas for improvement. Regular audits help ensure ongoing compliance with DORA’s requirements.
Conclusion
Achieving DORA compliance is a complex but necessary task for financial institutions and their third-party service providers. By implementing robust risk management frameworks, conducting regular resilience testing, and fostering collaboration across the financial ecosystem, organizations can meet DORA’s requirements and safeguard against emerging cyber threats. Compliance not only strengthens security but also promotes a more resilient financial system that can weather the challenges posed by ICT-related disruptions.