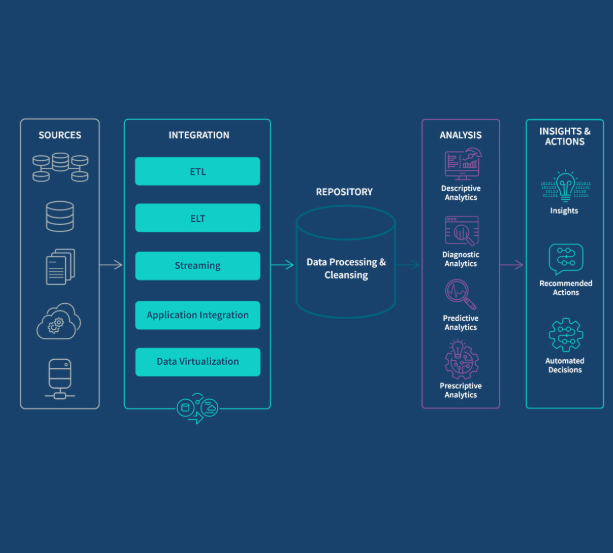
The Business Impact of AI-Powered Text-to-Speech Technology
Artificial intelligence has revolutionized how businesses communicate, and one of the most transformative advancements is AI-powered text-to-speech (TTS) technology. From improving customer interactions to streamlining operations, TTS is reshaping...