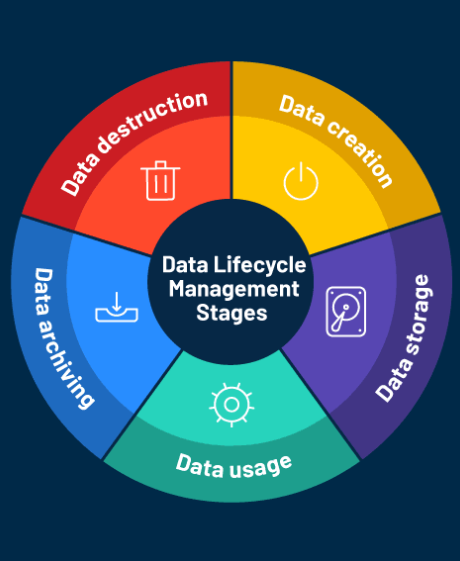
Data security has never been more critical, especially for large organizations managing vast amounts of sensitive information across multiple environments. With the increasing reliance on cloud computing, hybrid infrastructures, and on-premises systems, securing data from breaches and unauthorized access is a growing challenge. A Data Security Posture Management (DSPM) solution is essential to help safeguard data, ensure compliance, and streamline risk management. In this blog, we will explore the key features to look for when choosing a DSPM solution to protect your business’s sensitive data.
1. Automated Data Discovery and Classification
A key feature of any robust DSPM solution is automated data discovery. As organizations grow, their data often becomes scattered across different environments, including cloud services, third-party platforms, and hybrid infrastructures. DSPM tools help to identify and inventory data across these various environments, ensuring no sensitive information is left unmonitored.
Effective data classification is also crucial. A good DSPM solution will allow you to categorize sensitive data, such as personal information, financial records, and intellectual property, to prioritize security efforts based on data sensitivity. This targeted approach helps reduce risk and optimize security resources.
2. Continuous Monitoring and Real-Time Risk Assessment
Continuous monitoring is vital for maintaining a strong security posture. As data is created, accessed, and modified, it’s essential to track these activities to detect potential vulnerabilities in real time. A good DSPM tool will offer real-time security monitoring, alerting you to any suspicious activity or misconfigurations within your data repositories.
Risk assessments are also a core feature, helping identify vulnerabilities like exposed data or excessive permissions. With risk scoring, DSPM solutions enable security teams to prioritize risks based on their potential impact, making it easier to address vulnerabilities before they turn into security incidents.
3. Granular Data Access Control
Limiting access to sensitive data is crucial for protecting your organization’s information. A DSPM solution with granular access controls will provide deep visibility into user roles, permissions, and access patterns, allowing you to enforce policies that restrict data access to authorized personnel only.
By implementing role-based access control (RBAC) and the principle of least privilege, DSPM solutions can minimize the potential for unauthorized data access. Audit trails and real-time logs also allow you to track data access, which is essential for security investigations and compliance audits.
4. Data Loss Prevention (DLP)
Preventing data loss is a key aspect of protecting sensitive information. A DSPM solution should include robust Data Loss Prevention (DLP) capabilities to detect and block unauthorized data transfers, file sharing, or downloading, especially from unsecured or unapproved applications.
Additionally, effective DSPM tools enforce data encryption, both in transit and at rest. This ensures that sensitive data remains secure even if exposed during a breach, helping to maintain compliance with data privacy regulations like GDPR and HIPAA.
5. Policy Enforcement and Automated Remediation
Automating the enforcement of data security policies is another important feature of DSPM solutions. Whether it’s classifying data, managing access rights, or defining sharing protocols, automation can reduce manual oversight and ensure policies are consistently applied across the organization.
Automated remediation is essential for quickly addressing security issues when they arise. A good DSPM solution should be able to take corrective actions automatically, such as closing insecure ports or updating access permissions, ensuring that vulnerabilities are quickly mitigated without relying on human intervention.
6. Compliance with Regulations
Many organizations, especially those in regulated industries such as healthcare, finance, and retail, need to meet strict data privacy and security standards. DSPM solutions should be equipped with features that help you comply with regulations like GDPR, CCPA, HIPAA, and SOC 2.
Look for a DSPM solution that offers comprehensive compliance reporting. These reports will demonstrate how your organization protects sensitive data and help identify any compliance gaps, ensuring you’re ready for audits and minimizing the risk of penalties.
7. Advanced Risk Management and Threat Reporting
Beyond monitoring, DSPM solutions should provide comprehensive risk management features. This includes the ability to assess potential risks related to misconfigurations, excessive data exposure, and unauthorized access.
Real-time alerts are a must-have in a DSPM solution. These alerts notify security teams of suspicious activities or potential threats, ensuring that your organization can respond quickly to prevent data breaches or compliance violations.
8. Secure Collaboration and Data Sharing Controls
In today’s collaborative business environment, employees often need to share sensitive data with external partners or teams. A DSPM solution should offer features that help manage and control how data is shared both internally and externally.
For instance, solutions that integrate with tools like Google Workspace and Microsoft 365 can provide secure ways to collaborate without compromising data security. Additionally, features like data masking allow sensitive information to be shared securely without exposing raw data.
9. Integration with Existing Security Infrastructure
To ensure a holistic approach to security, your DSPM solution should integrate seamlessly with other tools in your organization’s security infrastructure. Look for compatibility with Security Information and Event Management (SIEM) platforms, Identity and Access Management (IAM) solutions, and Cloud Access Security Brokers (CASBs). These integrations allow you to combine data from multiple sources, providing a comprehensive view of your security posture.
Conclusion: Selecting the Right DSPM Solution
When choosing a Data Security Posture Management (DSPM) solution for your organization, it’s essential to consider features like automated data discovery, real-time risk assessment, data access control, and compliance support. A strong DSPM solution should help secure sensitive data, enforce policies, and ensure compliance with regulations, all while optimizing your risk management efforts.
With the right DSPM solution in place, your organization can improve its data security posture, protect sensitive information, and mitigate risks effectively—ensuring a secure and compliant digital environment.