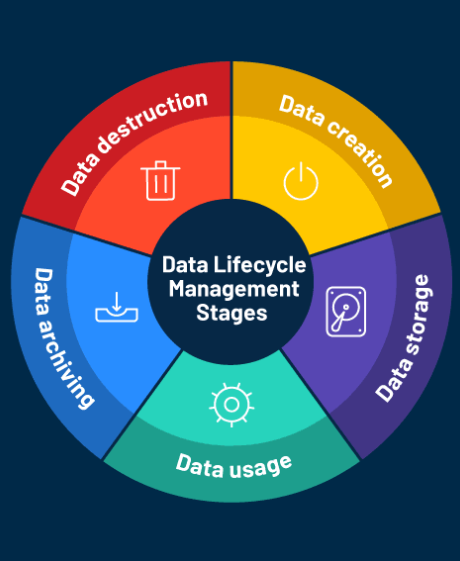
Information security officers (ISOs) play a crucial role in safeguarding sensitive data within organizations. As cyber threats continue to evolve, proactive measures are essential to manage, mitigate, and reduce data risks. Here are five key strategies that ISOs can adopt to strengthen data protection, reduce risk, and contribute to a robust data security posture.
1. Identify and Secure High-Risk, Sensitive Data
The first step in improving data protection is identifying and securing high-risk, sensitive, and critical data within the organization. This process involves:
Data Classification: Categorizing data based on its sensitivity is crucial for prioritizing protection efforts. Automated classification tools can streamline this process and ensure accuracy.
Risk Assessments: Regular evaluations help detect vulnerabilities and potential exposure points, allowing businesses to address risks proactively before they lead to breaches.
By identifying and securing sensitive data, organizations reduce the risk of data breaches, ultimately saving money on legal fees and remediation costs.
2. Implement Robust Access Control Measures
Restricting access to sensitive data is one of the most effective ways to mitigate data risk. Here are ways to strengthen access control:
Role-Based Access (RBAC): Enforce RBAC to ensure that employees can only access data necessary for their job responsibilities.
Access Audits: Regularly audit access logs to spot unauthorized access attempts and unusual activities.
By tightening control over data access, organizations enhance security and minimize the risk of compliance violations and costly breaches.
3. Apply Data Encryption Techniques
Encryption is a powerful safeguard for protecting data both at rest and in transit. To enhance data security, ISOs should:
End-to-End Encryption: Apply encryption protocols to ensure that data is protected throughout its lifecycle—from creation to storage and transfer.
Stay Current with Encryption Standards: Regularly update encryption techniques to defend against emerging threats and ensure data remains secure.
Using encryption effectively reduces the financial consequences of data breaches and helps maintain robust security.
4. Create a Solid Incident Response Plan
A proactive incident response plan is vital for managing data breaches quickly and effectively. Key steps include:
Response Team: Assemble a dedicated team responsible for managing breaches and incidents. Regular training and testing of response strategies will ensure swift action when needed.
Ongoing Improvements: Continuously review and update the incident response plan based on lessons learned after each incident.
Having an efficient response plan minimizes the impact of breaches, saving time and resources, and reducing the costs of remediation and downtime.
5. Utilize Data Loss Prevention (DLP) Tools
Data Loss Prevention (DLP) solutions can significantly enhance data security by preventing unauthorized data movement. DLP tools provide:
Monitoring Data Movement: Track data transfers to ensure that sensitive information is not shared improperly.
Automating Security Policies: DLP tools help automate the enforcement of security policies, reducing human error and ensuring consistent data protection.
Investing in DLP solutions can save organizations from the costs of data leaks and associated reputational damage.
Conclusion
In today’s risk-laden digital landscape, information security officers must be proactive in securing organizational data. By identifying and protecting high-risk data, enforcing access controls, implementing encryption, preparing for incidents, and utilizing DLP tools, businesses can enhance their data security posture.
These strategies not only protect sensitive data but also help organizations reduce risks and realize long-term cost savings. In an ever-evolving cybersecurity environment, taking the right steps now can significantly improve resilience and safeguard valuable data assets.