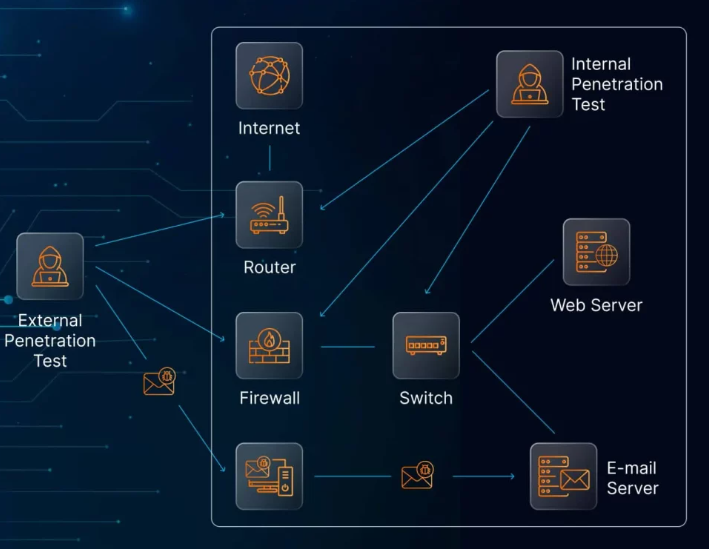
As digital transactions become more prevalent, businesses that handle cardholder data face increasing pressure to safeguard sensitive information. Cybercriminals are constantly developing new techniques to exploit vulnerabilities, making it essential for companies to go beyond basic security measures. That’s where the Payment Card Industry Data Security Standard (PCI DSS) comes in, and more specifically, where penetration testing plays a crucial role.
While PCI DSS outlines various technical and organizational requirements for compliance, penetration testing stands out as a strategic tool for discovering and addressing weaknesses before they can be exploited. In this blog, we’ll explore how PCI DSS penetration testing works, what the latest standards require, and how organizations can ensure they’re properly protected.
What Is PCI DSS Penetration Testing?
Penetration testing under PCI DSS involves safely simulating cyberattacks to identify exploitable vulnerabilities in systems that handle cardholder data. Unlike automated scanning tools that simply detect known issues, penetration tests take it a step further by actively attempting to exploit weaknesses. This gives organizations a real-world view of their security standing and exposes how an attacker might gain unauthorized access.
Conducting regular tests is vital because meeting compliance requirements does not automatically mean your systems are secure. Misconfigurations, unpatched software, or new attack techniques can easily slip through unnoticed unless actively tested against.
PCI DSS 4.0: What Has Changed?
The latest version of PCI DSS brings more flexibility and a stronger emphasis on continuous security improvement. Key updates include:
- Tailored Approaches: Companies can now use alternative security methods if they can demonstrate effectiveness, offering room for innovation while still adhering to the standard’s goals.
- Stricter Access Controls: Multi-factor authentication is now required for all access to sensitive data, not just administrative accounts.
- Improved Encryption Protocols: Stronger encryption for data at rest and in transit is now mandatory, using modern cryptographic techniques.
- Expanded Testing Scope: The latest guidelines include risk-based testing that reflects current threats, encouraging more comprehensive assessments.
- Increased Service Provider Oversight: Third-party vendors and cloud service providers are held to higher security expectations and must demonstrate ongoing compliance.
By March 31, 2025, all organizations subject to PCI DSS must transition to version 4.0 to remain compliant.
Requirements for PCI DSS-Compliant Penetration Testing
To meet PCI DSS standards, penetration tests must follow a formal process and be carried out by individuals or teams with appropriate qualifications. Internal staff may handle internal tests only if they are independent from the systems being evaluated. For external testing, organizations often rely on specialized third-party providers.
Qualified testers should hold credentials such as OSCP, CEH, or CREST certifications, and demonstrate proven experience in ethical hacking. Testing must cover all systems that interact with cardholder data, including internal networks, external entry points, cloud environments, and connected third-party services.
Proper Scope and Testing Strategy
A thorough test scope should include:
- Cardholder Data Environment (CDE) perimeter
- Segmentation controls to verify isolation from non-secure networks
- Critical applications that handle, store, or process cardholder data
- Recent vulnerabilities and threats from the past year
The testing should be conducted at least once a year and whenever significant infrastructure or system changes occur.
If network segmentation is used to limit PCI DSS scope, its effectiveness must be verified through targeted testing. This helps ensure the CDE remains isolated and secure from other parts of the network.
Documentation and Reporting
After testing is complete, the organization should receive a detailed report outlining:
- Identified vulnerabilities, categorized by severity
- Methods of exploitation, demonstrating how attackers could leverage these weaknesses
- Business impact assessments, explaining what could happen if the vulnerabilities were exploited
- Remediation advice, with clear steps for resolving each issue
Once remediation is complete, a retest should be performed to confirm the fixes were effective and no new issues have emerged.
Preparing for a Penetration Test
Proper preparation is key to a successful and efficient PCI DSS test. Before starting, businesses should:
- Clearly define scope: List all systems, networks, and services that process or store cardholder data.
- Assess risk: Prioritize areas that are most likely to be targeted based on recent threats and past incidents.
- Document assets: Maintain a complete inventory of systems, applications, and third-party integrations to ensure nothing is overlooked.
Doing this upfront allows the testing team to execute a thorough and focused assessment that reflects the organization’s unique risk profile.
What to Do If You Don’t Pass
Failing a penetration test isn’t uncommon, but it’s critical to take immediate action. Any high or critical-risk issues must be remediated before a company can be considered PCI compliant. After addressing the findings, organizations must retest to confirm that the vulnerabilities have been effectively resolved.
Ignoring these issues not only puts customer data at risk but can also result in fines, increased scrutiny from payment processors, or suspension from handling credit card transactions.
Avoiding Common Testing Pitfalls
Several common mistakes can compromise the value of a penetration test. These include:
- Inadequate scope: Failing to include all relevant systems, such as APIs, cloud services, or third-party platforms.
- Relying solely on automation: Automated tools are limited and can’t replicate how real attackers think or behave.
- Neglecting cloud infrastructure: Cloud-hosted environments must be tested with the same rigor as on-premise systems.
- Skipping the retest: Addressing issues without validating fixes leaves organizations vulnerable to recurring threats.
Avoiding these pitfalls ensures the testing process provides accurate, actionable insights and supports overall compliance goals.
Beyond Compliance: Penetration Testing as a Security Investment
While meeting PCI DSS requirements is essential, penetration testing should be seen as more than just a compliance task. When done correctly, it offers a clear picture of where your defenses stand and how they can be improved. It also demonstrates due diligence to partners, customers, and regulatory bodies—building trust and strengthening your overall security posture.
By establishing a routine for testing, integrating manual and automated methods, and acting on the results, businesses can protect cardholder data more effectively and avoid costly breaches. In a digital economy where reputation and data integrity are everything, investing in proactive security testing isn’t just wise—it’s necessary.