The digital landscape is shifting. What was once a domain dominated by skilled hackers and sophisticated cybercriminal organizations is now accessible to almost anyone with malicious intent. Thanks to the rise of easy-to-use hacking tools, more individuals – ranging from disgruntled employees to curious teenagers – are engaging in cybercrime. This trend has profound implications for businesses of all sizes, escalating the risk of data breaches and other cyberattacks. It’s crucial for organizations to understand how these tools are reshaping the cybersecurity landscape.
The Changing Face of Cybercrime
For years, cybercriminals were often portrayed as highly skilled hackers, capable of exploiting complex vulnerabilities with intricate coding. While these attacks still exist, a growing number of cyberattacks are being carried out by individuals with minimal technical expertise. The surge in user-friendly hacking tools and step-by-step online tutorials is allowing even those with limited skills to launch attacks. These tools, often available for little or no cost, are now empowering a new generation of “citizen hackers” to cause significant damage to organizations.
This shift means that businesses of all sizes, not just large corporations with extensive IT resources, need to invest in robust cybersecurity solutions. The threat is real and expanding.
The Dark Side of the “As-a-Service” Model
Just as legitimate industries have embraced the “as-a-service” model, so too has the world of cybercrime. The rise of “Hacking-as-a-Service” (HaaS) platforms has made it easier than ever for individuals to access powerful malicious tools. These platforms offer everything from botnets to ransomware kits, and they cater to people with little to no hacking experience.
Here are some of the services commonly offered on HaaS platforms:
1. DDoS (Distributed Denial-of-Service) Attacks
For a fee, individuals can rent a botnet – a network of compromised computers – and use it to overwhelm a target’s website or server with traffic, effectively rendering it inaccessible. These services often include simple dashboards for attackers to customize their attacks.
2. Ransomware Kits
Pre-packaged ransomware is available, complete with instructions and customer support. These kits allow individuals to encrypt a victim’s data and demand a ransom in exchange for its release. With no coding skills required, even a beginner can launch a successful attack.
3. Phishing Kits
These kits provide templates and tools to create convincing phishing emails and websites, often mimicking legitimate businesses, to steal sensitive data like usernames, passwords, and credit card details.
4. Exploit Kits
Exploit kits come with pre-written code designed to take advantage of known vulnerabilities in software and operating systems. “Citizen hackers” can use these kits to gain unauthorized access to systems without needing to write their own code.
5. Malware Builders
These tools allow users to create custom malware, often using simple drag-and-drop interfaces, enabling people with minimal technical knowledge to craft malware for specific targets.
6. Credential Stuffing Tools
Credential stuffing tools automate the process of trying thousands of stolen username/password combinations against websites to gain access to user accounts. These tools exploit the common habit of reusing passwords across multiple platforms.
The Dark Web: A Marketplace for Cybercrime
The dark web, an encrypted part of the internet that requires specialized software like Tor to access, is a thriving marketplace for cybercriminals. Here, “citizen hackers” can easily find the tools, tutorials, and support they need to execute cyberattacks. This ecosystem is eerily similar to legitimate e-commerce platforms, but instead of consumer goods, it offers tools and services for launching cyberattacks.
Open-Source Tools and Tutorials: Fueling the Cybercrime Machine
It’s not just the dark web that’s enabling cybercrime. Many open-source tools designed for legitimate security research are also being misused for malicious purposes. Tools like Nmap, Wireshark, and Metasploit, originally created for ethical hacking and penetration testing, are readily available and can be used by anyone with malicious intent.
Additionally, a wealth of tutorials on platforms like YouTube and online forums offers step-by-step guides on how to use these tools for hacking. This wealth of information reduces the barrier to entry for aspiring hackers, making it easier than ever to launch attacks.
How This Affects Businesses
The proliferation of easily accessible hacking tools has several important implications for businesses:
Increased Frequency of Cyberattacks
With the rise of citizen hackers, the number of potential attackers has skyrocketed. Cybercrime is no longer the exclusive domain of elite hacker groups. Anyone with malicious intent can now easily become a threat to your business.
A Broader Range of Attack Vectors
Citizen hackers might not have the skills to develop sophisticated exploits, but they can access a wide range of tools to target vulnerabilities in your systems. This means businesses must defend against a much broader array of potential attacks.
Attribution Challenges
Tracking down the source of cyberattacks becomes much harder when the attacker is using readily available tools and anonymizing techniques like VPNs. This makes it difficult for businesses to identify and respond to threats in a timely manner.
Faster Attacks
With simple-to-use hacking tools, attacks can be launched much faster than before. This leaves businesses with a smaller window of time to detect and mitigate threats before significant damage is done.
Strengthening Your Business’s Security: A Multi-Layered Approach
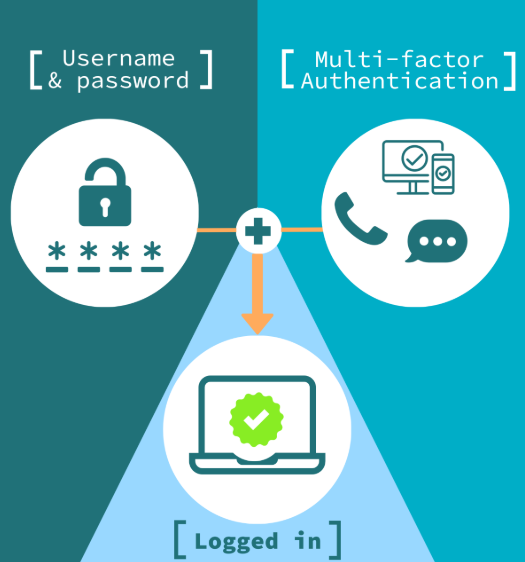
To defend against the growing threat posed by “citizen hackers,” businesses need a comprehensive security strategy. Traditional measures like firewalls and antivirus software are no longer enough. The evolving threat landscape demands a multi-layered security approach that includes not only stronger perimeter defenses but also proactive measures to identify vulnerabilities within your systems.
In addition to using advanced cybersecurity tools, businesses must educate their employees about common threats and ensure they have incident response plans in place. Security is not a one-time setup but an ongoing process of adaptation and vigilance.
Cybersecurity professionals can play a critical role in this process, providing expertise in risk assessment, security solution implementation, and ongoing monitoring to keep your business protected from emerging threats.
Conclusion
The rise of the “citizen hacker” underscores the urgent need for robust cybersecurity measures. With the proliferation of easy-to-use tools and resources, businesses must adapt to an increasingly hostile digital environment. Ignoring these threats is no longer an option. By strengthening your security posture and staying informed about the latest threats, you can protect your business from the growing risk of cybercrime.