As technology evolves, so too do the methods and tactics used by cybercriminals. Looking ahead to 2025, businesses and individuals must be ready for the growing sophistication of cyber threats. To stay protected, it’s critical to understand the emerging risks, the tools used by attackers, and the consequences of insufficient security.
In this post, we’ll highlight the major cybersecurity threats predicted for 2025 and how businesses can take proactive steps to safeguard their digital assets.
The Rise of AI-Powered Cyberattacks
Artificial Intelligence (AI) is transforming numerous industries, including cybersecurity. While it’s a helpful tool for security professionals, cybercriminals are also using AI to execute more complex and targeted attacks.
AI enables attackers to launch personalized phishing campaigns, create convincing vishing (voice phishing) scams, and employ social engineering tactics that bypass traditional defenses. Additionally, the emergence of deepfakes—realistic media that can manipulate a person’s likeness or voice—poses a significant challenge, especially when it comes to identity theft and fraud.
As AI-driven attacks become more advanced, businesses will need to adopt new strategies for authentication and verification to stay ahead of the curve.
AI in Information Operations
AI is also being used in the realm of Information Operations (IO), where the manipulation of information can influence public opinion and political landscapes. Cybercriminals are leveraging AI to generate convincing disinformation, produce high-quality fake content, and amplify false narratives across social media platforms.
The ability of AI tools to scale content creation and target specific audiences with precision is making it more difficult to discern between legitimate and fabricated information. This evolving trend highlights the need for businesses to strengthen their media literacy and improve the methods by which they evaluate online content.
Ransomware and Extortion Tactics
Ransomware attacks, which encrypt data and demand payment for its release, continue to be a major threat. However, in 2025, these attacks are likely to become even more complex, with attackers using multifaceted extortion tactics. This includes not only encrypting data but also stealing sensitive information and threatening to release it unless a ransom is paid.
The rise of cloud computing and interconnected systems increases the potential attack surface for ransomware. Businesses must implement strong data backup systems, regularly update software, and secure their networks to reduce vulnerability to such attacks.
Infostealer Malware
Infostealer malware remains a significant threat, targeting sensitive data like login credentials, financial information, and personal details. These malicious programs typically infiltrate systems through phishing emails, malicious websites, or compromised downloads.
Once installed, they can quietly collect data and transmit it to cybercriminals. With the shift to remote and hybrid work, along with personal devices being used for business purposes, the risk of infostealer malware has increased. Businesses must prioritize endpoint security, conduct regular employee training, and implement secure network protocols to minimize the impact of these threats.
The Democratization of Cyberattacks
The accessibility of cyberattack tools and services on the dark web is lowering the barriers for less-skilled individuals to launch sophisticated attacks. Tools such as ransomware-as-a-service (RaaS), exploit kits, and botnets can now be rented or purchased by anyone with malicious intent, making the threat landscape even more complicated.
This means businesses must defend against a broader range of attackers, from highly skilled hackers to individuals with minimal technical knowledge. Adopting proactive security measures such as vulnerability scanning, penetration testing, and up-to-date security software is essential in this new era of cybercrime.
The Growing Risk of Compromised Identities
In today’s hybrid work environments, compromised identities are an increasing concern. Cybercriminals often steal login credentials to gain unauthorized access to sensitive company systems. This can result in data breaches, financial theft, and significant disruptions to business operations.
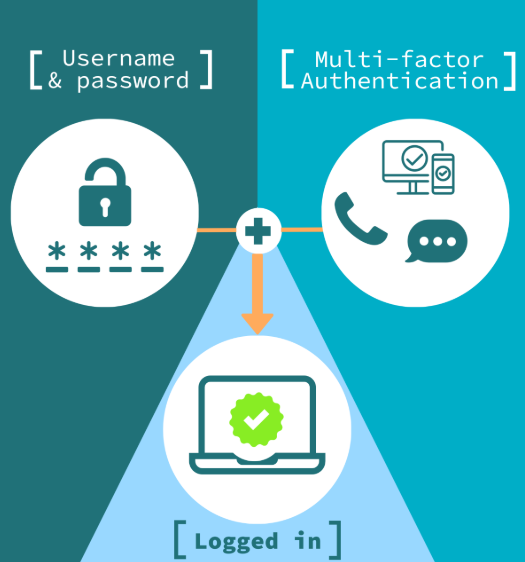
With the growing use of cloud services and bring-your-own-device (BYOD) policies, managing identity and access control is more critical than ever. Multi-factor authentication (MFA), strong password policies, and continuous monitoring are essential strategies to mitigate the risks associated with compromised identities.
Web3 and Cryptocurrency Exploits
As Web3 technologies and cryptocurrencies continue to grow, they present attractive targets for cybercriminals. Attackers are increasingly finding ways to exploit vulnerabilities in blockchain platforms, decentralized applications (dApps), and cryptocurrency exchanges.
Phishing attacks targeting cryptocurrency users, as well as vulnerabilities in smart contracts, are key risks. The decentralized nature of Web3 makes it challenging to track stolen assets, so businesses and individuals involved in this space must prioritize robust cybersecurity practices to secure their digital wallets and assets.
Faster Exploitation and Widening Target Range
The speed at which cybercriminals can exploit vulnerabilities is accelerating, and the number of potential targets is expanding. Attackers now have more tools and techniques at their disposal, and the growing number of discovered vulnerabilities makes it difficult for businesses to keep up.
This makes vulnerability scanning, timely patch management, and comprehensive security assessments even more crucial. Businesses must act quickly to address vulnerabilities before they can be exploited.
Preparing for the Cybersecurity Challenges of 2025
The cybersecurity landscape in 2025 will be defined by increasingly sophisticated and diverse threats, many of which will leverage AI and other advanced technologies. Businesses must remain vigilant, keep their security measures updated, and educate their employees on best practices for data protection.
With the right strategies, businesses can minimize the risk of cyberattacks and ensure that they are prepared for the evolving threat environment.
Downtown Computer Services: Your Cybersecurity Partner
At Downtown Computer Services, we specialize in helping businesses in Fort Lauderdale navigate the ever-changing cybersecurity landscape. Our team provides a full range of IT support services, from assessing your current security posture to implementing advanced security measures, employee training, and incident response planning.
Partner with us to ensure your business is ready to face the cybersecurity challenges of 2025 and beyond. Let us help you build a secure IT infrastructure that protects your data, your reputation, and your business.
Conclusion
Cyber threats will continue to evolve in 2025, with AI, ransomware, and new attack methods leading the way. By staying proactive, understanding emerging risks, and implementing robust cybersecurity practices, businesses can protect themselves from these growing dangers. The key to success in this ever-changing digital world is vigilance, preparation, and smart defense strategies.