With Florida emerging as a key hub for cryptocurrency adoption, small businesses are presented with new opportunities to embrace digital currencies. However, alongside these opportunities come significant security challenges. The decentralized nature of cryptocurrencies, while offering advantages, also makes them appealing targets for cybercriminals. It’s crucial for businesses to understand how to protect their digital wallets and secure their assets in this evolving landscape.
The Growth of Cryptocurrency in Florida
Florida has positioned itself as a leading state for cryptocurrency with laws that make it easier for businesses to adopt digital currencies. Governor Ron DeSantis signed legislation in 2022 to define virtual currencies and clarify regulations surrounding cryptocurrency transactions. This forward-thinking stance provides an ideal environment for businesses to integrate cryptocurrencies into their payment systems.
Cryptocurrencies like Bitcoin, Litecoin, Ethereum, Ripple, and Monero have become popular in Florida, with businesses recognizing the potential to appeal to younger, tech-savvy consumers. With the state’s proactive approach, Florida continues to promote blockchain technology through initiatives like the Florida Blockchain Task Force, helping businesses tap into the growing crypto market.
However, the rise of digital currencies also introduces new vulnerabilities. Unlike traditional banking systems, cryptocurrencies are decentralized and often unregulated, making them attractive to hackers and cybercriminals.
Understanding Cryptocurrency Wallets
For any business dealing with cryptocurrencies, understanding how to secure digital wallets is critical. Wallets are used to store, send, and receive cryptocurrencies, and they come in various types, each with its own level of security.
Software Wallets
These wallets are installed on your computer or mobile device, allowing businesses to manage their private keys directly. While they offer convenience, software wallets can be vulnerable to malware and hacking if the device is compromised. Examples of software wallets include Electrum and Exodus. To protect against threats, it’s important to keep the device’s software updated and use antivirus programs.
Hardware Wallets
Hardware wallets are physical devices that store private keys offline, offering enhanced protection from cyberattacks. These are ideal for businesses holding substantial amounts of cryptocurrency. Popular hardware wallets like Trezor and Ledger require a PIN or passphrase to access the private keys. They are considered one of the most secure ways to store digital assets, but it’s crucial to safeguard the device and keep a backup of the recovery phrase.
Online Wallets
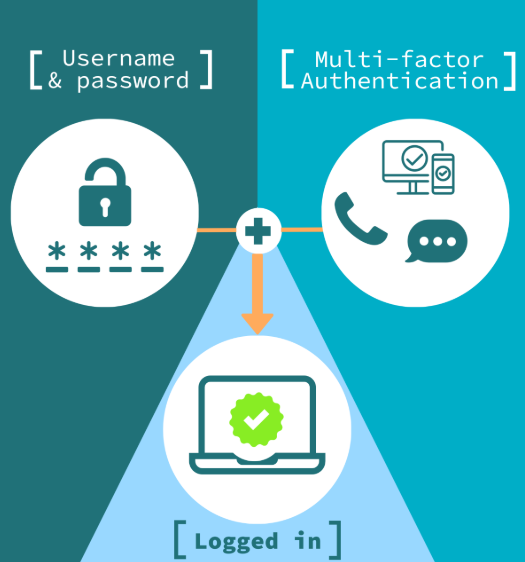
Online wallets, or web wallets, are hosted by third-party services like Coinbase or MetaMask. While they offer easy access and convenience, the security of these wallets depends on the platform provider. If the service is compromised, your funds could be at risk. Always choose reputable platforms with strong security practices and consider using two-factor authentication (2FA) to add an extra layer of protection.
Wallet Drainers: Silent Threats to Your Digital Assets
A growing threat in the cryptocurrency world is the “wallet drainer” malware. These malicious programs can silently steal your funds by exploiting vulnerabilities in your wallet or the websites you interact with. In 2024, wallet drainers were responsible for stealing nearly $500 million from over 300,000 victims. These attacks often occur when users connect their wallets to fake websites that mimic legitimate platforms, allowing attackers to steal assets with minimal detection.
To protect against wallet drainers, always verify the URL and security certificates before connecting your wallet to any website. Never share your private keys or seed phrases, as these are critical to your wallet’s security. Furthermore, use strong, unique passwords for your accounts and enable 2FA whenever possible.
Types of Malware Targeting Cryptocurrency Users
Aside from wallet drainers, other types of malware continue to evolve and target cryptocurrency holders. These include SpyAgent, DoubleFinger, and Clipper, which use different methods to steal digital assets.
SpyAgent
SpyAgent targets cryptocurrency recovery phrases, often found in screenshots on your phone. By using optical character recognition (OCR) technology, it can extract sensitive information from your screenshots and grant attackers access to your wallets.
DoubleFinger
This malware infects Windows systems and uses advanced techniques like DLL sideloading to bypass security software. It then deploys cryptocurrency stealers to extract private keys and recovery phrases.
Clipper
Clipper malware intercepts clipboard data, replacing wallet addresses with those controlled by the attacker. This allows cybercriminals to redirect transactions without the user’s knowledge.
To guard against such threats, never take screenshots of your recovery phrase and always double-check wallet addresses before confirming any transactions.
Best Practices for Securing Cryptocurrency Transactions
When handling cryptocurrency transactions, several security measures are essential for protecting your digital assets.
Keep Your Seed Phrase Safe
Your seed phrase is the key to your crypto wallet. If someone gains access to it, they can control your wallet and steal your funds. Always store your seed phrase offline, and never share it with anyone. Avoid using cloud-based password managers for storing your recovery phrase, as these can be vulnerable to hacking.
Double-Check Transactions
Cryptocurrency transactions are irreversible, so it’s critical to verify transaction details before sending funds. Ensure that the recipient’s address and the transaction amount are correct. A simple mistake, like a typo in the address, can result in the permanent loss of your assets.
Choose the Right Network
Different cryptocurrencies operate on different blockchain networks, each with its own set of rules. Ensure that you’re using the correct network when making transactions. For example, Ethereum transactions must be sent over the Ethereum network, and sending tokens to an incompatible network can lead to irreversible losses.
Blockchain Explorers: Tools for Verifying Transactions
Blockchain explorers allow users to track transactions and verify the status of funds. By entering a transaction ID or wallet address, you can check if a transaction has been completed successfully. For businesses accepting cryptocurrency, blockchain explorers provide a valuable tool for ensuring that transactions are processed correctly and for monitoring wallet balances.
Partnering for Cybersecurity: Protect Your Business
As cryptocurrency adoption continues to grow, small businesses must be vigilant about securing their digital assets. Cybersecurity solutions, such as robust encryption and multi-layered defenses, can help protect your cryptocurrency holdings. Working with a trusted IT partner can provide the expertise needed to safeguard your wallets and transactions from emerging threats.
Conclusion
Cryptocurrency provides exciting opportunities for small businesses, but with these opportunities come new risks. Protecting your digital assets requires understanding wallet types, recognizing the threats posed by malware, and implementing secure transaction practices. By following best practices and staying informed, businesses can safely navigate the world of cryptocurrency and leverage it as a valuable asset in their payment systems.